Are ISPs competent?
A random Computer Science student exposes how Kosovo's top ISPs fail at security - even against DDoS. Still think you can trust them?

This article is also available in Albanian
⚠️ Disclaimer: This entire article is my opinion as an expert in IT, rooted in good faith that these ISPs will actually fix the issues I've mentioned here
In todays day and age, we rely on the internet for everything. From our scrolling on our phones phones, to working on our computers, turning on our lights, adjusting our ACs, and now even updating our cars cars over the air, it seems like a connection to the net is almost required.
So, do you trust the people who provide this necessity to you? I sure as hell do not (but that's because I have trust issues, you're completely fine), in Kosovo most network engineers are older than my dad, and the new people who actually know what they're doing in today's age occupy lower level roles where they have no authority to make decisions on their own.
Today, I'll be talking about some "misconfigurations" in Kosovo's major internet service providers' infrastructure, vulnerable to extremely primitive DOS/DDOS attacks.
However, first I must give credit where credit is due. I contacted each ISP, and telkos answered. Their administrator, going by "YK" replied in less than 30 minutes, and I must say I'm impressed.
The man first told me they'd know who touched their servers now that I outed myself, a joke I really did not expect, and that I found extremely funny and friendly.
After I introduced myself, he immediately forwarded my concerns to the engineering team, which is the right thing to do in this case.
I must say though, the engineering team must've been asleep, as now 3 days later I have seen no changes at all. Poor administrator, he was so cool just for engineering to end up ignoring him.
With that, let's jump into it. I am hoping I don't get a call or knock from the local police because they think I'm some type of scary dangerous hacker.
Explanations
Before anything, I must actually explain some terms
ISP - This means "internet service provider", it's the company who gives you your internet connection.
DoS - DoS means denial of service, it's a primitive attack present since the beginning of internet. It's where a computer spams another computer (usually a server) with network requests, this means the server will not have the resources to reply to legitimate network traffic. Think of it like talking on the phone, you can talk just fine one on one with one of your friends right? Let's now add some loud music, maybe a little wind? Can't hear your friend so good anymore can you? That's how DoS works.
DDoS - DDoS just means DoS, but Distributed, hence the extra D at the front. Because engineers quickly came up with the idea of "rate-limiting", or in other words limiting the amount of traffic one computer can send to their server, DDoS was born. DDoS, as the name implies uses many computers, usually spread out across the world/a region to attack one single server (You might think "Hey, wouldn't that be expensive?", well yes it would, however these attacking computers usually belong to normal people who just downloaded and ran a virus on their PC). Going back to our example of a phone call, let's imagine its now a group call, a zoom meeting! Now instead of just one person sending gibberish across their mic, 1000 people are screaming at you, playing music, etc, you think you can talk to any one of them at all, even if they were trying to have a normal conversation?
So, who's affected?
Below is a list of affected ISPs, and their severity from most severe, to least severe.
Now, you might notice Kujtesa has an asterisk next to their listing, that is because I found almost nothing at all in my research, I'll explain everything later on.
Perhaps most importantly, you as a user are NOT affected here at all (yet).
Details, oh so much details
Now you might be curious on the actual details, and I'm here to tell them all.
What I did was find the exposed PUBLIC addresses by doing a simple (and I mean simple) scan of their IP subnets.
Why does this matter?
An IP address is basically the address of where your server lives, it's where you can make requests to it, and how your router ("Wi-Fi box") can know where to find for example Youtube, or Facebook.
You should not have your real, static, public address exposed, because it'll invite DDoS attacks from people who:
- Don't like you
- Profit from your services being down
- Want to watch the world burn
The only exception is when you have counter measures against DDoS attacks, like Cloudflare.
Cloudflare is a FREE service that will essentially take all requests to your servers and handle the layer of DDoS protection for you, meaning you never have to give out your exposed and unprotected address publicly, you just give people Cloudflare's address and then give Cloudflare your address, so it would go something like this
Customer -> Cloudflare -> Telkos.net
Why? Because Cloudflare will simply not forward any malicious requests to your server, and it will actually also handle rate-limiting for you, all for free.
In addition, your server should have it's firewall configured so it does not accept any network traffic at all from any IP address not in Cloudflare's IPv4 or IPv6 or in your own trusted IPs list (like the IP addresses of web-developers).
The issue here is that these ISPs don't have any DDoS protection set up, a lot of them did not even have rate-limiting set up on the pages I found.
Findings
I found quite a lot of exposed, unprotected services, below are all of them listed by each ISP
Telkos
- Main site
- Staff login dashboard
- Staff MySQL database
- 3CX Management Interface (Phone System)
- Exposed NextCloud login (Likely a system for backups, or employees')
- Webmail server (used to host the website they use to send emails, not the actual mail server)
- An actual freaking LDAP instance, with an option to bind anonymously
(meaning ANYONE, without a password, can browse the data it holds, which is likely staff info, or confidential) - Customer management/authentication services (Potential for everyone to lose access to their internet/TV if they are downed)
- PAYMENT PROCESSOR
Ipko
- Main site
- Online chatting/support system (multiple servers)
- Self care portal
- Cisco router (not as bad as you'd think actually)
- Customer management/authentication services (Potential for everyone to lose access to their internet/TV if they are downed)
- PAYMENT PROCESSOR
Artmotion
- Main site
- Web Mail
- Mail management portal (mailcow)
- Self care portal
- Customer management/authentication services (Potential for everyone to lose access to their internet/TV if they are downed)
- Internal Management services
- UNIFI management interface (probably for customers)
- Multiple API's
- VOD/Streaming server management services
- VOD/Streaming servers
- Various internal systems
Vala/PTK
- Main site
- TV management services
- TV/VOD? login
- Simple redirect for their android app
Kujtesa
- Main site
- Random Windows Server RDP instance (really guys, windows server?)
Proof
Why would you just believe me?
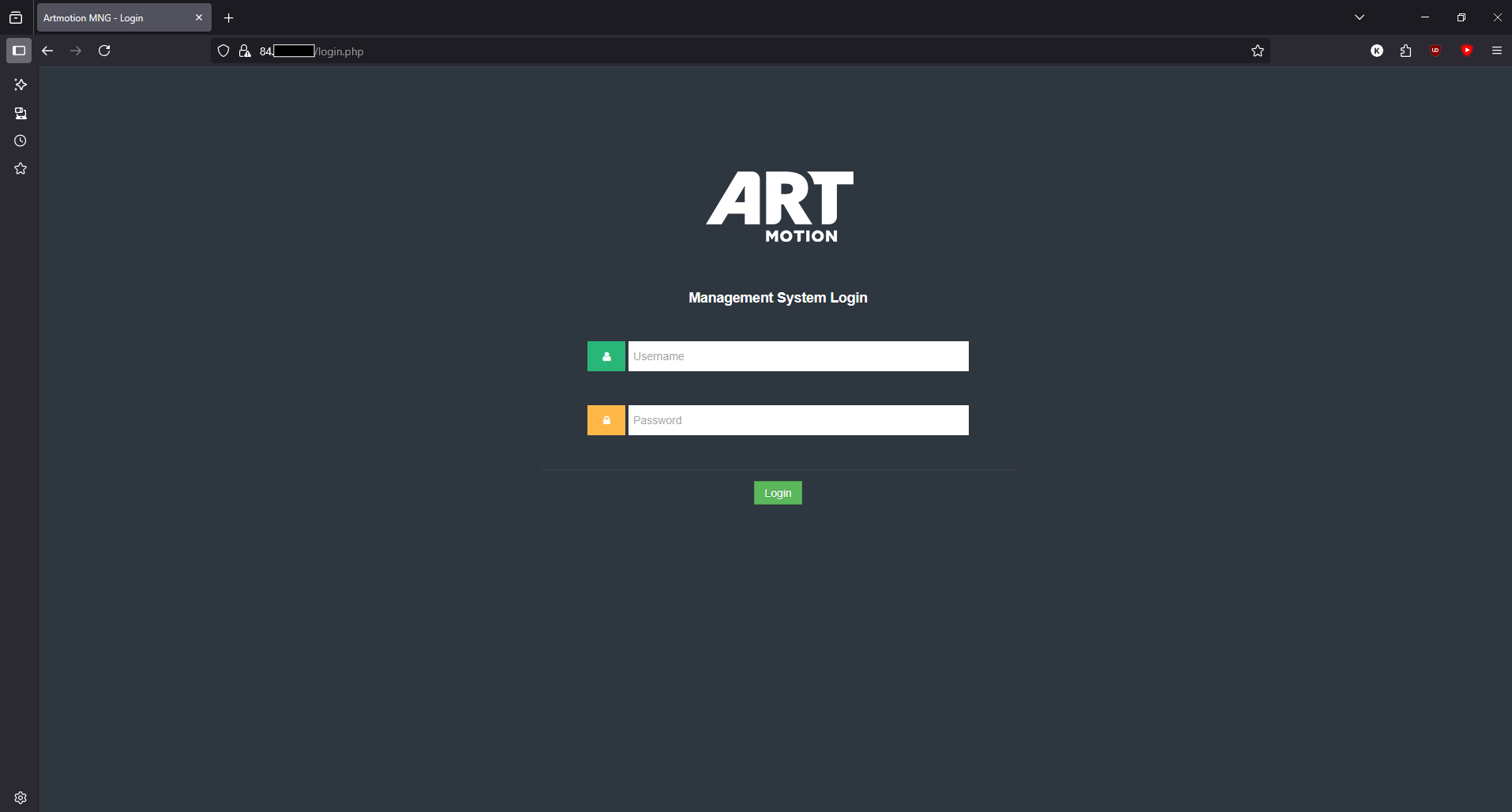
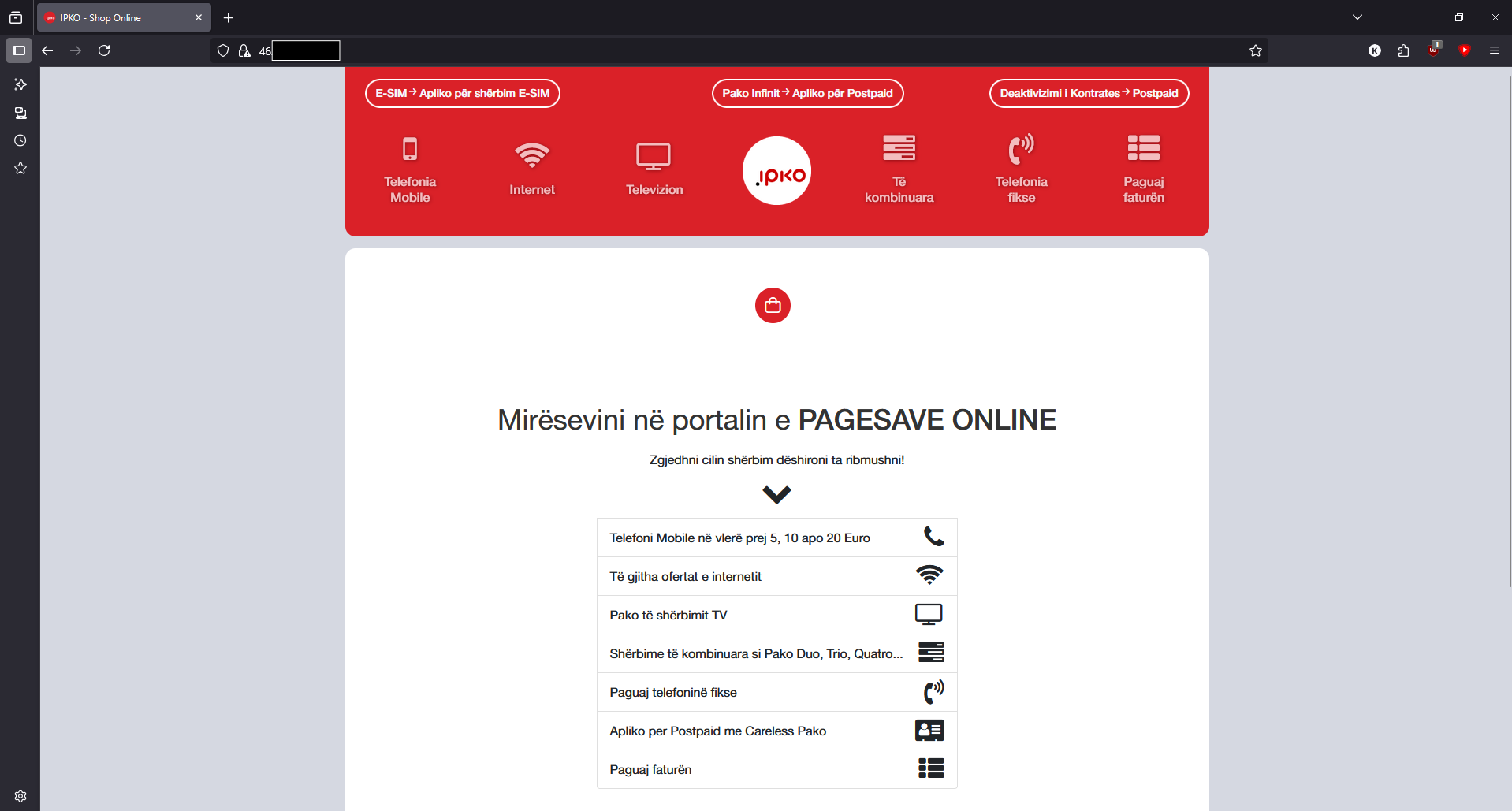
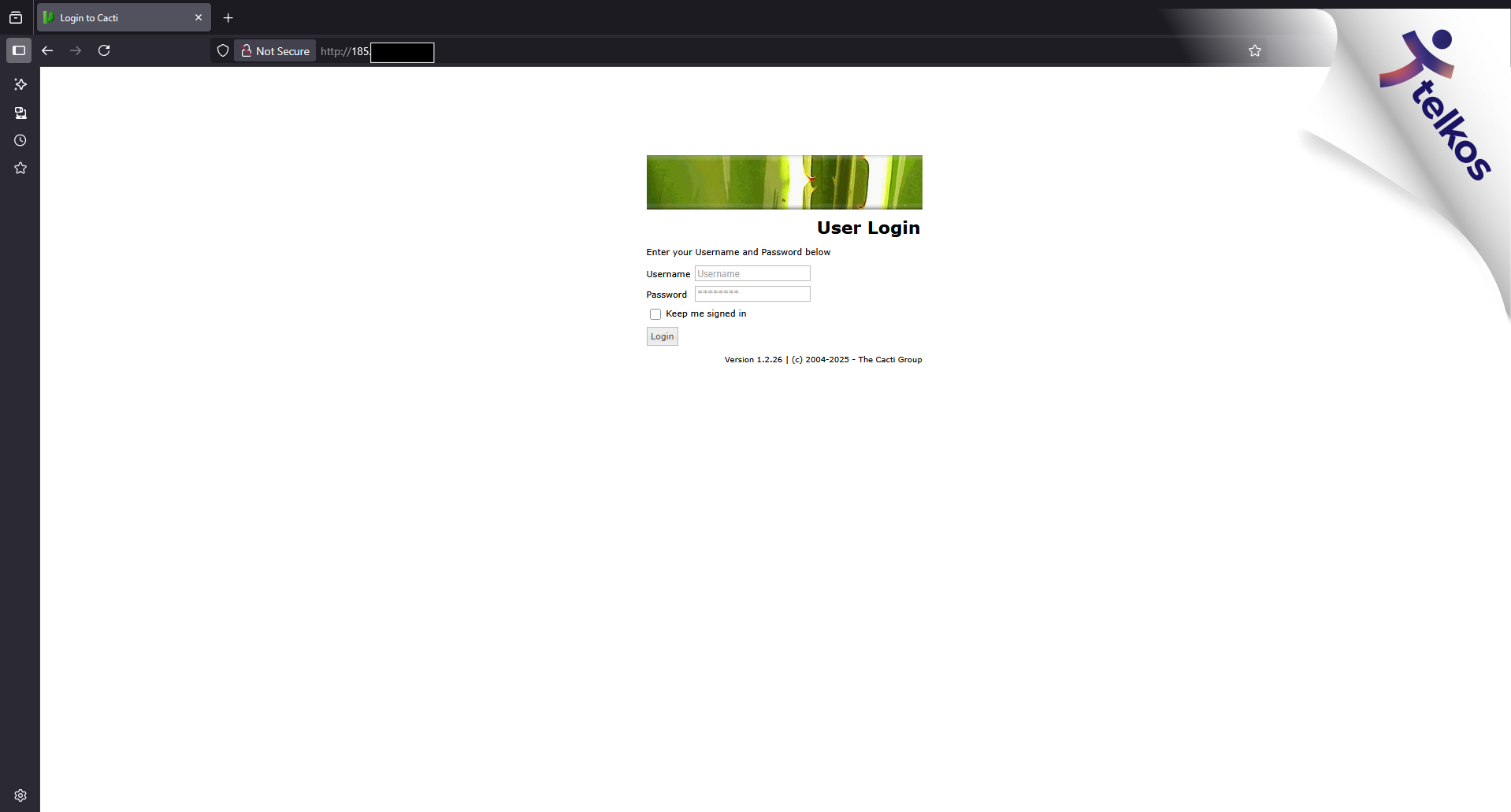
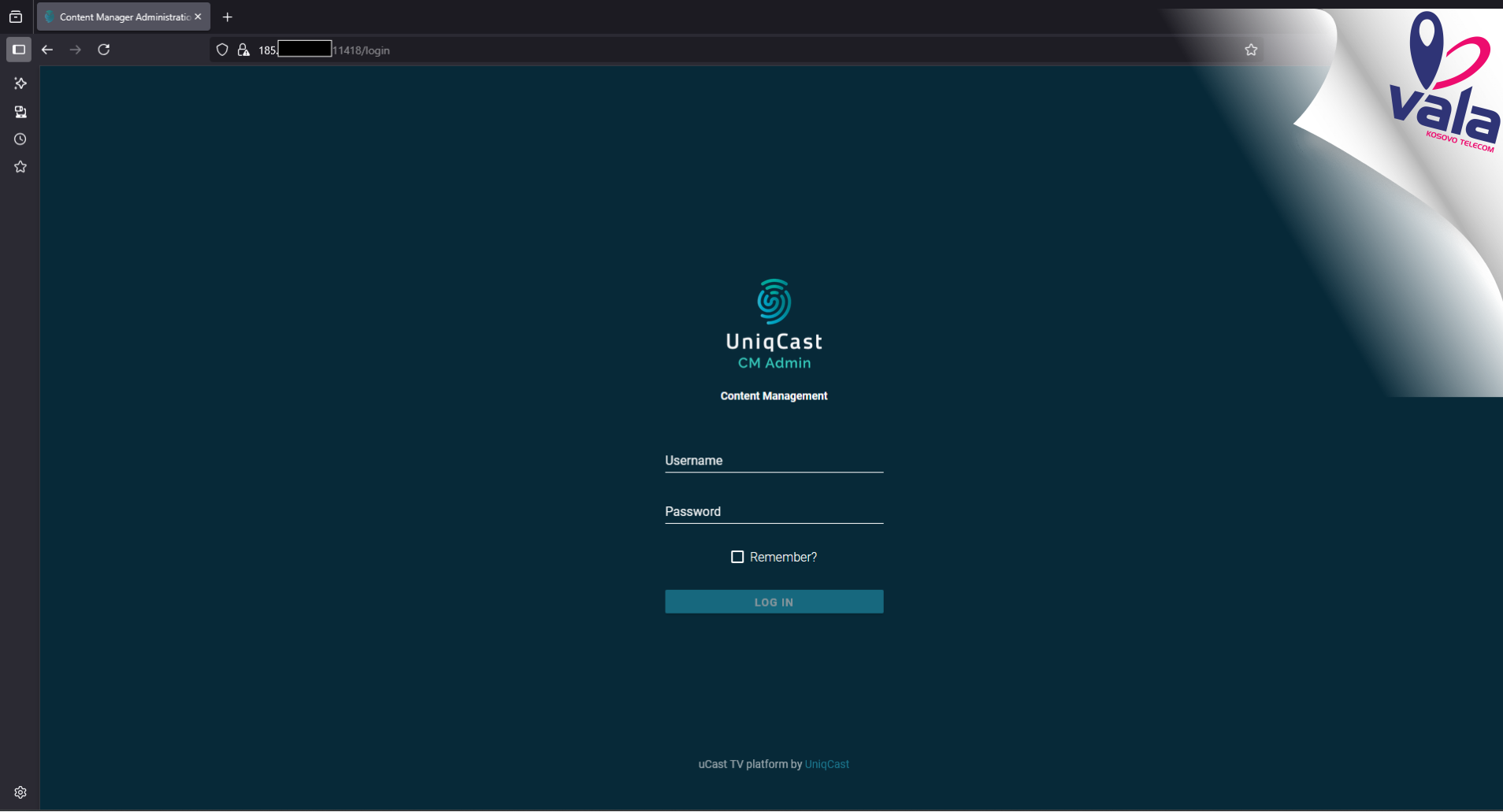
Notes
IPKO's gross allowance of transmission of payment info over an unprotected, unsecure address (I mean via HTTP) is borderline criminal and likely violates the following Kosovo laws (IN MY OPINION):
- Law No. 06/L-082 - Kosovo's General Data Protection Law
- Law No. 03/L-209 (Amended by Law No. 04/L-155) - Kosovo's law on Payment Services | Note: Not sure if this would apply to the ISPs themselves, but definitely the payment processors
Why? Well, Law No. 06/L-082 outlines that private data (such as payment info) should be transmitted/kept securely, and Law No. 03/L-209 outlines:
The primary objective of the Central Bank shall be to foster and to maintain a stable financial system, including a safe, sound and efficient payment system.
Transmission of payment details over HTTP is a horrible horrible thing to ALLOW, as MITM attacks are incredibly easy to pull off, I'm talking if you pay for your internet on a public network (likely Wi-Fi), you're getting your FULL payment details stolen.
To note, I have not actually tested this, as I don't actually have a valid subscription with IPKO anymore. However it would be so incredibly easy (yet unlikely) for something like a malicious fake redirect sending you to the bare IP address, and you ignoring the google security warning (as those are a little common) for someone on your network to be capturing your payment info.
The end
I am beyond disappointed at the lack of common sense from these ISPs, I mean who really cares if let's say Artmotion's main website goes down? So what, I cant look at some trash internet+tv offers. However, the issue is their payment processors and customer management systems, those should be protected with some kind of DDoS protection, either in house, or Cloudflare, as if those go down, customers might experience internet downtime, tv downtime, or staff might have issues actually onboarding new customers when the field technicians actually go out for installs.
Thanks for reading this absurdly long blog post, I hope to see these companies fix their infrastructure and harden it against the most common and primitive attacks known to the internet.
I'd like to apologize to some of my colleagues that I know who work at these companies, as they might get a headache or two if this is ever noticed by anyone, especially one of my mentors who I've likely sent this to myself, sorry guys!
Updates
I've had some colleagues reach out to me regarding this post. Turns out, Ipko and Telkos do have some anti DDoS protection. They use FastNetMon, a layer 3-4 DDoS protection solution.
Lets break down why it sucks,
Credits to Shams Hanna of InformatiQ for the help on this portion.
FastNetMon is a DDoS monitoring/protection solution designed to prevent TCP/UDP flood attacks or similar, it is not designed or intended for use agaist OSI layer 7 (HTTP/s) attacks. It works by essentially monitoring network equipment (think router) logs/stats to detect sudden (often large) spikes in traffic.
If FastNetMon does detect a DDoS attack, after a sufficient enough transfer of data, it'll trigger a BGP announcement that will "blackhole" it's host's address, meaning that it will essentially tell other routers to no longer send it requests from the internet, therefor taking the host offline to protect it.
This does work even on a layer 7 attack (because the stats for layer 3-4 will also rise due to the traffic), however the host will still go down due to it, achieving the same goal as if the attack had continued and overwhelmed the host.
This is akin to pulling the fire alarm and evacuating the building every time someone burns toast — it stops the issue, but at a high cost.
Made with ❤️ by Korab Arifi.

