Work.ink & Opera. Is it malware?

Short answer, no, it's not malware. Work.ink is a registered company with an actual location tied to it's owner Alex, them spreading malware would be incredibly stupid as german police would be knocking on his door in no time.
With that out of the way, lets prove my claim.
We'll be utilizing triage to actually examine the official opera install, and the one from work.ink.
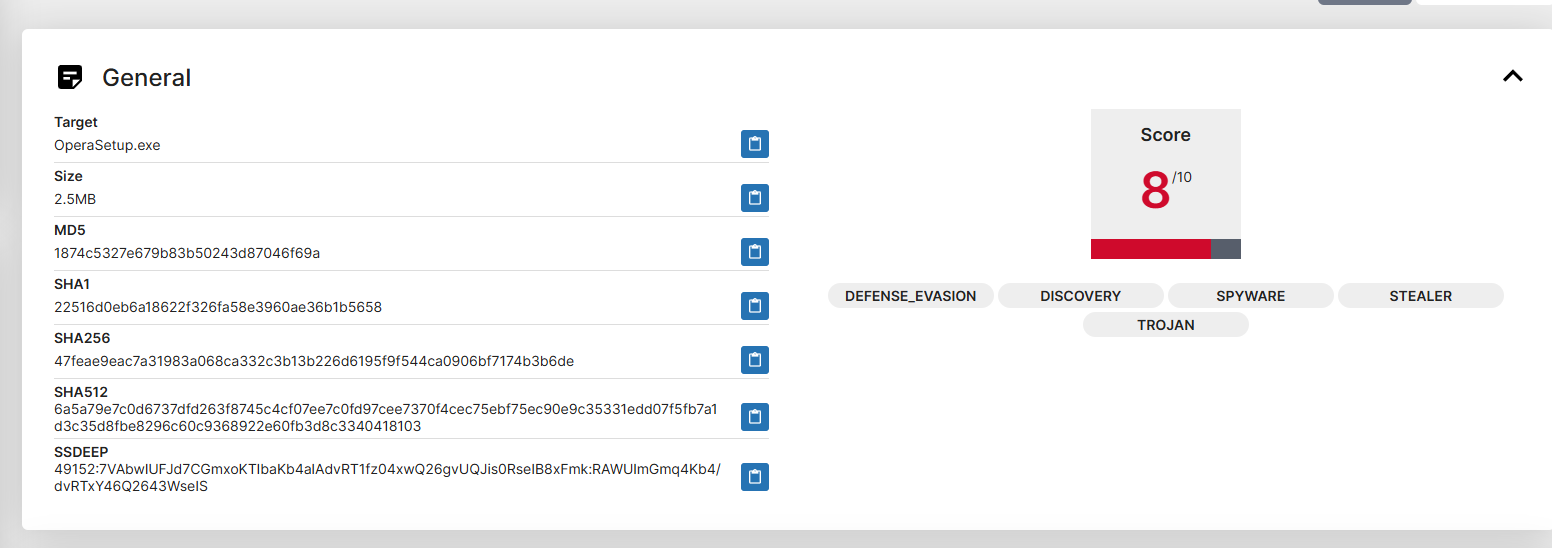
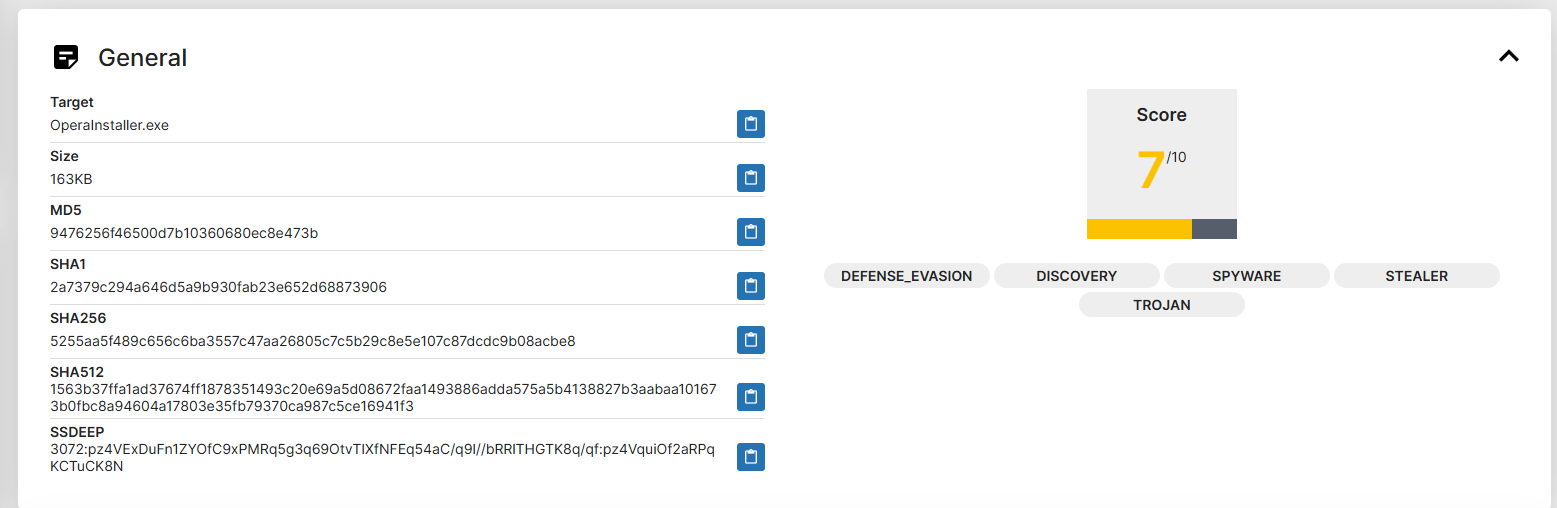
This is the analysis for the official Opera download, looks scary right? It's even marked for "Spyware", "Stealer", "Trojan".
The reason for this is simple, the opera setup will download opera, and scan your local files to import your existing browser profiles (like chrome, edge, firefox).
This raises massive red flags for AV/analysis software because a normal program should never be accessing those files, however when a user downloads opera, they want the migration to be quick, simple, and easy. So for those reasons the setup will read the files associated with your existing browser profile (history, bookmarks, passwords, credit cards)
We can see this in the analysis
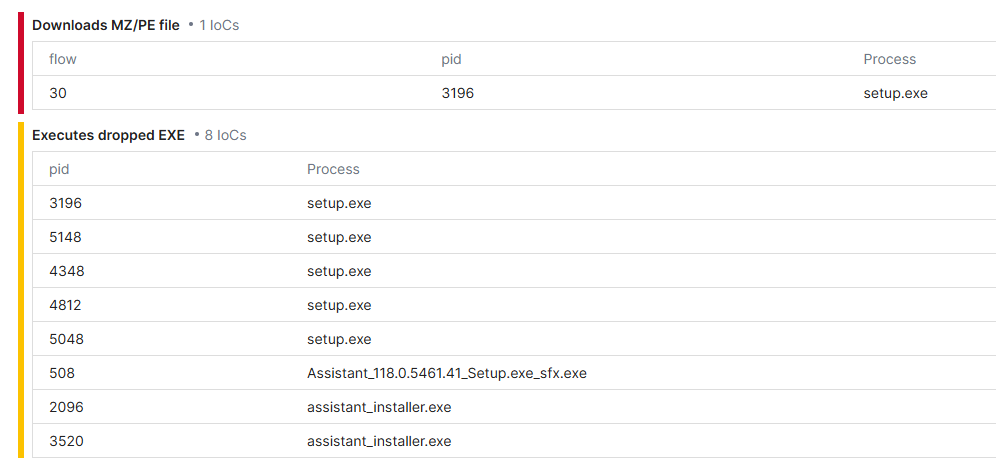
This is the opera setup getting the latest version of itself and then downloading opera off their servers.
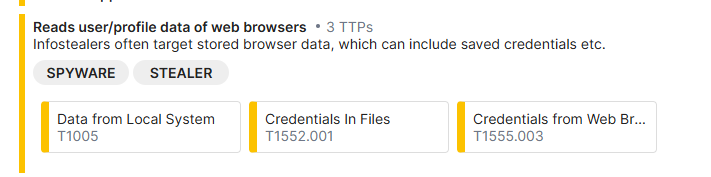
We can also see where the "Spyware" and "Stealer" tags come from, as I said its importing data from the users existing browser (think chrome)
Now about the other tags, they come from this:
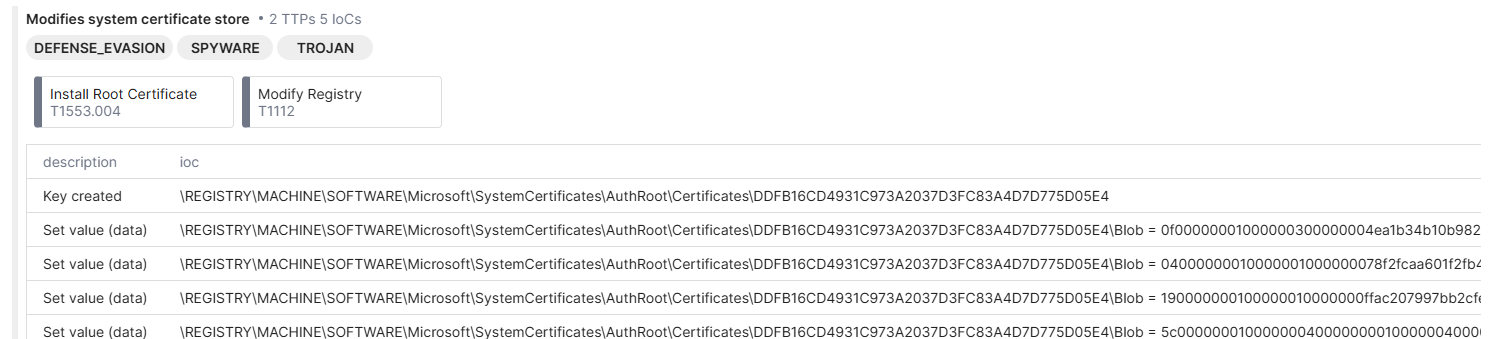
This is odd on first glance, why would a browser need to be installing certificates? Well, my thought is that it's either for use with their built in VPN stuff, or something to do with secure update, ssl pinning, or even just chromium stuff.
Work.ink's Opera installer
In triage, we can see that these are very similar, however work.ink uses a custom opera installer to validate that you've actually completed the installation (as it's required to pass the steps)
Funnily enough, the unofficial work.ink installer has a lower score, due to not utilizing the same tracking as opera does for installs. So we're off to a great start already.
On the work.ink installer we see the same thing,
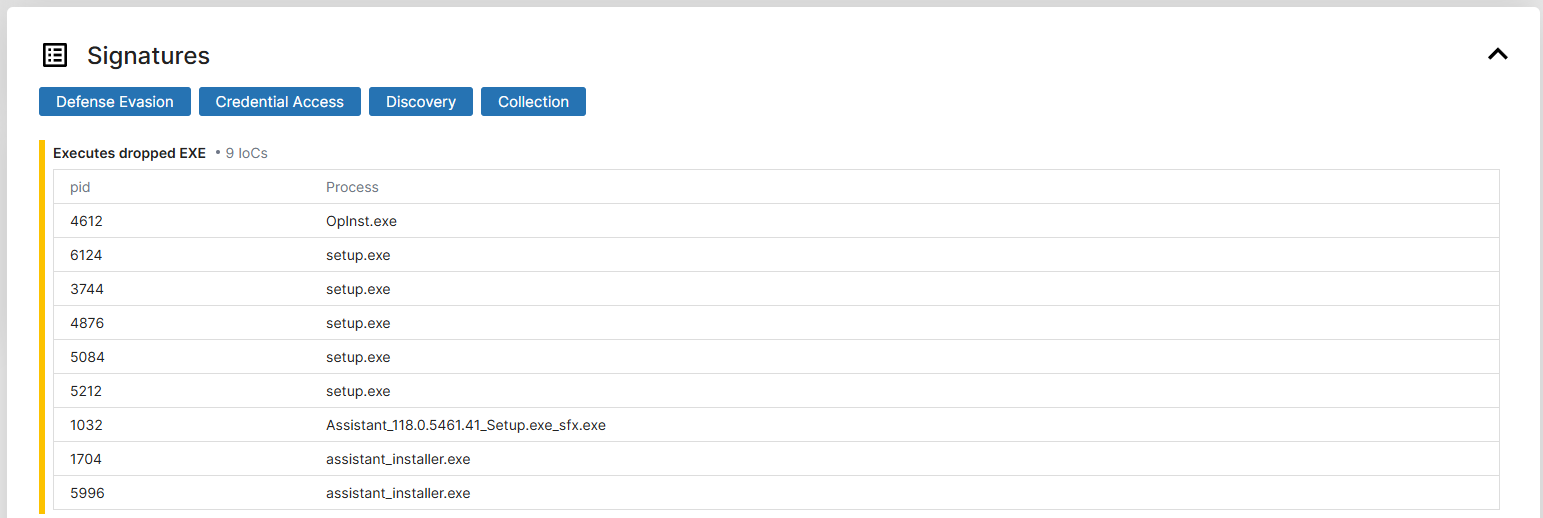
Work.ink's opera installer gets the latest copy of the official opera installer, and executes it.
Now's the fun bit, the work.ink installer is getting that official installer from "https://opera-download.work.ink/", thats how they verify that you've actually installed opera, from then on, it's essentially just the real opera installer doing its thing in a silent mode (no clicking agree on tracking etc)
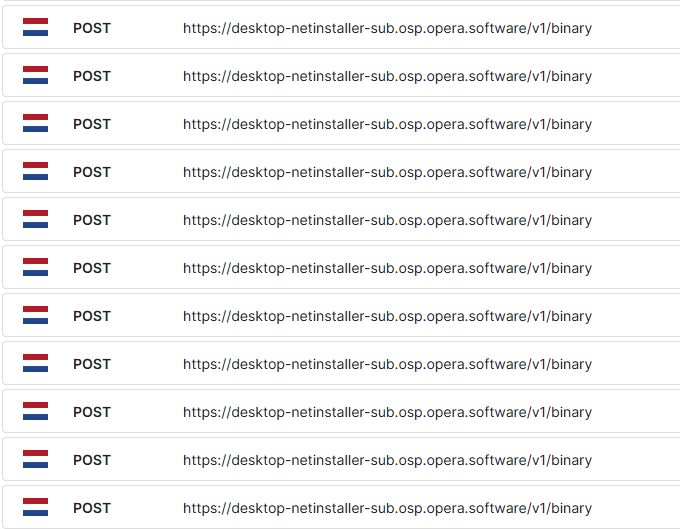
We can see this in the network requests for the work.ink installer analysis
It first gets the real opera setup from opera-download.work.ink

Then the official opera installer grabs the files from the official url and actually downloads opera on the users pc
Just like the official installer's analysis
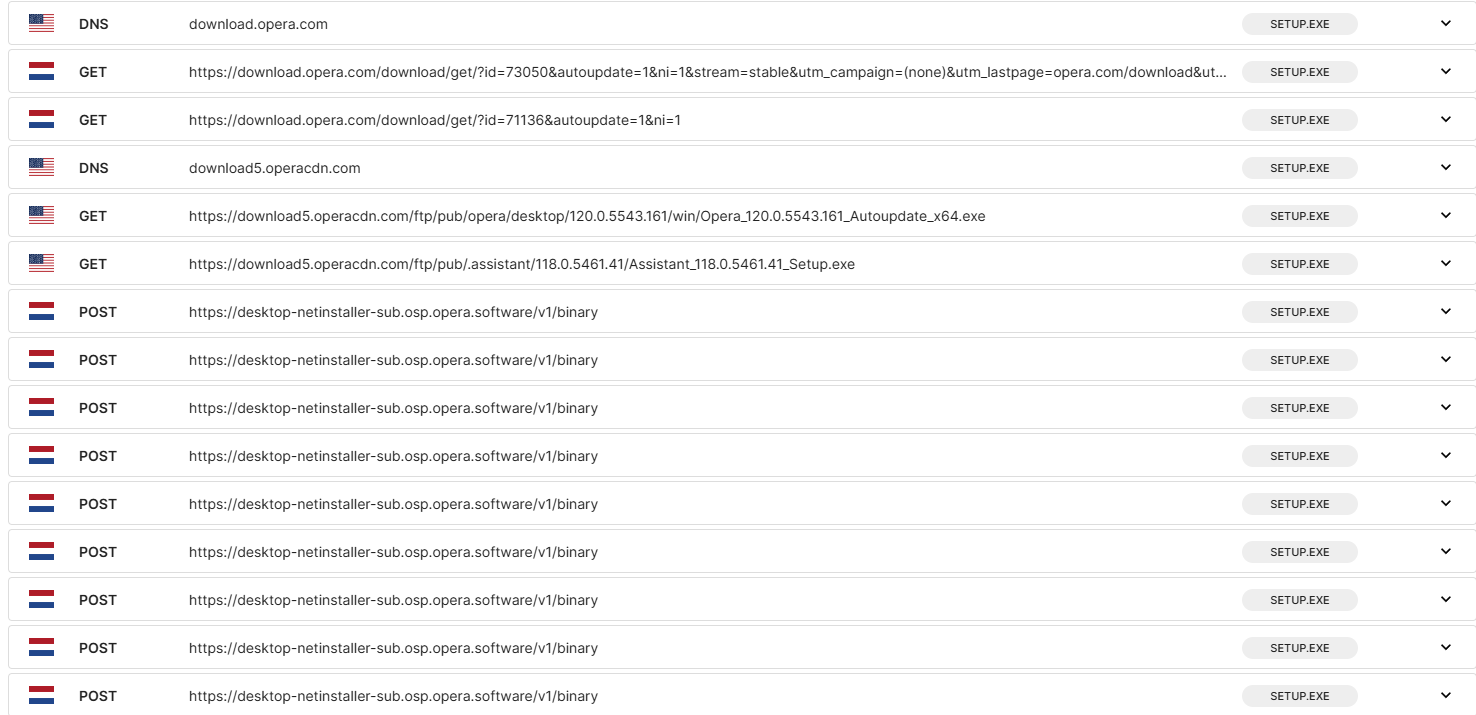
It's worth it to note here, the tracking on the official download, which is what gets the score to an 8 instead of 7, and how opera has more CDN servers than work.ink so it makes more requests.
I hope this article has helped you understand that work.ink is a legitimate company and how their opera installer actually works.
Disclaimer: I am a work.ink employee, however all the info provided here is public, and I have no benefit in working with anyone spreading malware, that'd just ruin my reputation. Furthermore I'm not on the engineering team and have no authority over anything you see here. I will be linking both the official opera installer analysis and the work.ink installer analysis below for transparency.
Official opera installer analysis - https://tria.ge/250807-tf8jtack6x/behavioral1
Work.ink opera installer analysis - https://tria.ge/250807-tc5czsxq12/behavioral2
Made with ❤️ by Korabi.

